Locking down Remote Desktop (RDP)
Introduction
This guide details how you can lockdown Remote Desktop access in Windows Server 2016 and 2019 using Windows firewall, we would always recommend this is done in conjunction with changing the remote desktop port as outlined in another of our knowledgebase articles
Background information
RDP (Remote Desktop Protocol) is the primary method for accessing a Windows server and provides a powerful utility for managing your entire Windows Server – especially from an Administrator account. This means that controlling access to it is vitally important. If an attacker can reach RDP then they only need to guess your administrator password to gain access – even if they can’t, the login attempts can severely slow down your server.
This is why we would always recommend restricting access to Remote Desktop from trusted IPs. Fortunately, it’s really easy to do.
The following has been tested on Windows Server 2012 R2, 2016 and 2019
Using the default RDP firewall rule
- Login to your server and goto: Start > Windows Firewall with Advanced Security
- Select Inbound rules from the left-hand column
- Scroll to “Remote Desktop – User Mode”
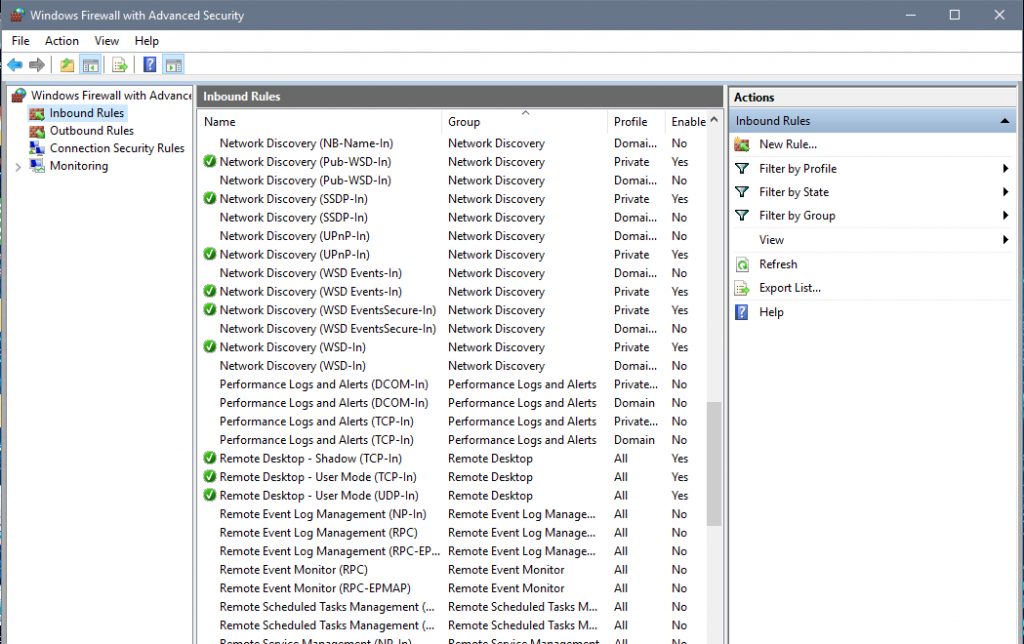
In order to restrict Remote Desktop connections, you only need to restrict the “TCP-in” connection
- To change what IPs are allowed, Right click the rule and go to Properties > Scope

- Add which ever remote IP addresses need access to RDP
- Hit ‘Apply’ and you are all set!
Using a custom firewall rule
If you have set your remote desktop to be on a non-default port (you can find out how to do that here) then you will need to make a new firewall rule.
- Open up Windows Firewall with Advanced Security
- Select Inbound Rules
- On the right hand side, choose “New Rule…”
- Using the Wizard, first choose “Custom”
- Choose “All Programs”
- Under “Protocol and Ports” select “TCP” and then enter the local port that you have set RDP onto. Leave Remote port as “All Ports”
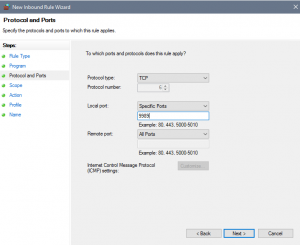
- Under “Scope” you have the ability to choose which IPs can access RDP
- Choose to “Allow the Connection” under Action
- This can be applied to all connection profiles
- Give the rule a name and then you are done and the rule will be applied.
How Else can you make Remote Desktop more Secure?
Restricting access to certain IPs isn’t the only way you can increase security on your server. The following will also help out:
- Change the remote desktop port
- Restrict permissions to certain users and avoid using the Administrator account where possible
- Use a strong password that isn’t in use on other servers
- Use a third-party 2-Factor Authentication solution


