How to Find All Clients Connected to HTTP or HTTPS Ports
Introduction
This short guide details how to find all clients (IP addresses) connected to an Apache or Nginx web server on HTTP (80) or HTTPS (443) ports on a Linux server.
Background information
In Linux every service running on the server is listening on the specific port. If connection is successful then the socket ( a combination of a port and IP address) is being created. Very useful Linux tools which are used to display information related to network sockets are ‘ss’ and ‘netstat’.
Using ss
If you issue the ss command without any arguments or options, it will return a complete list of sockets with established connections. 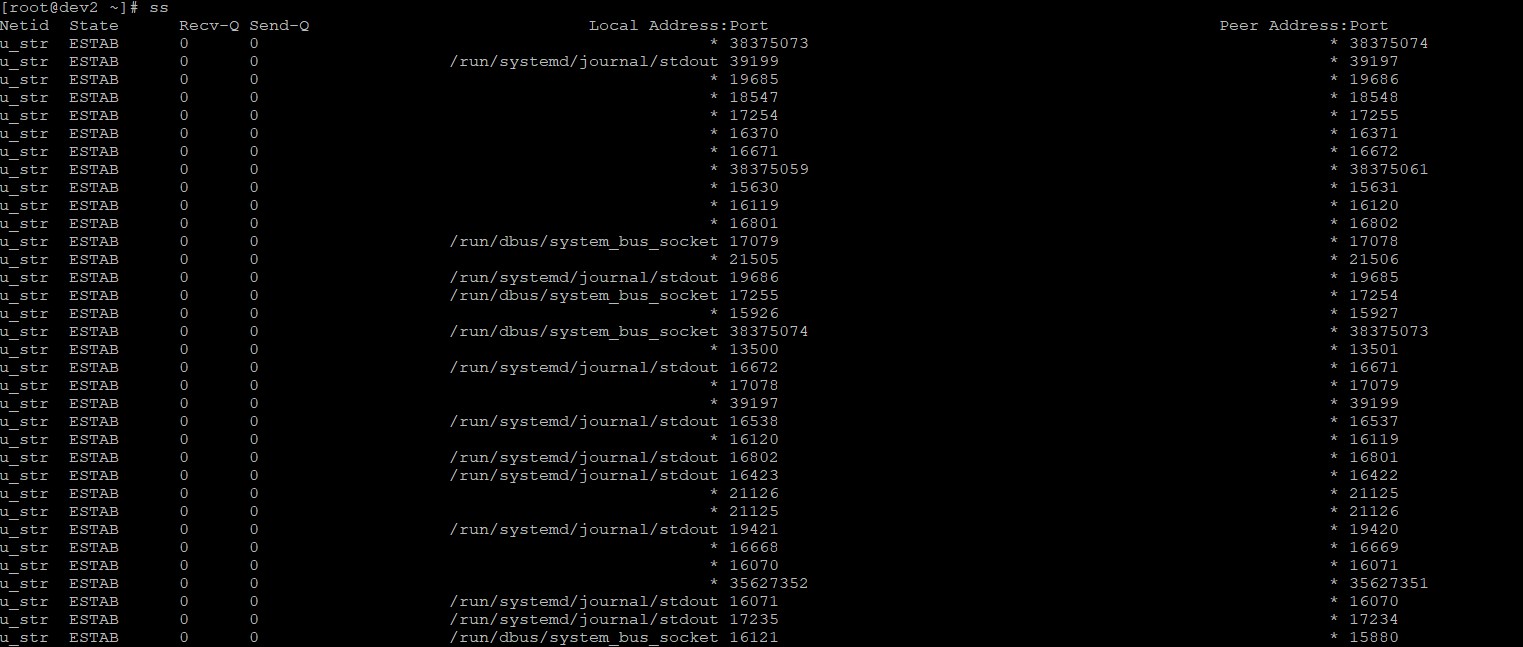
If we want to filter that list only to show clients connected to Ports 80 and 443 (HTTP and HTTPS), regardless of the state they are in then, the below command would be useful:
ss -o state established '( sport = :http or sport = :https )'

For the same results, but with numerical port numbers, you can run:
ss -tn src :80 or src :443

Using netstat
Execution of the netstat command without any options or arguments displays all existing connections including their state, source address and local address. Additionally, active UNIX domain sockets and relevant information such as inode number and full path are part of the netstat’s default network reports.
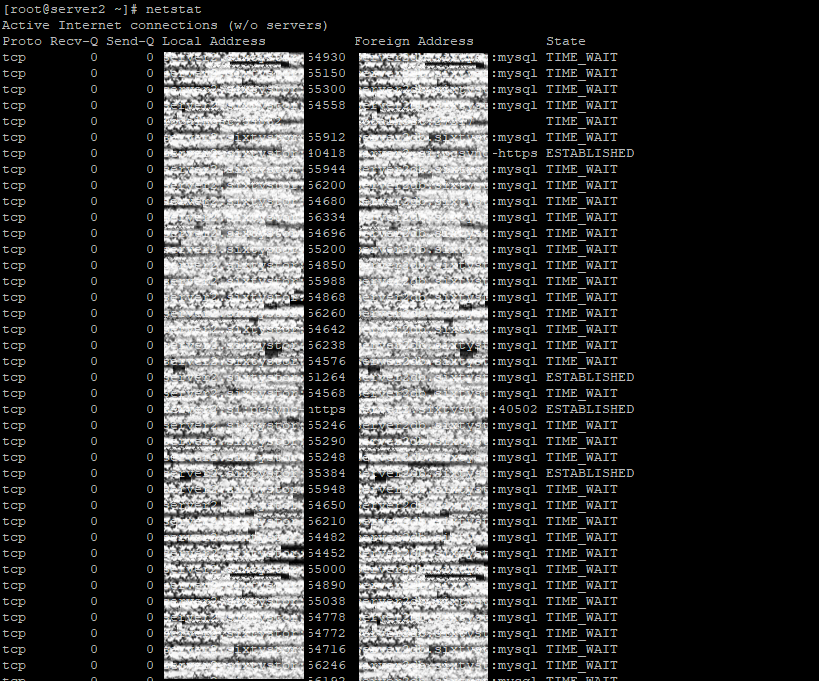
To filter that list to only show connections to HTTP and HTTPS ports, we want to use the following command:
netstat -tn src :80 or src :443
If the apache service reports as failed it would be a good idea to run one of the following commands which provide a list of IP connections to Apache sorted by quantity:
netstat -an | egrep ':80|:443' | egrep '^tcp' | grep -v LISTEN | awk '{print $5}' | egrep '([0-9]{1,3}.){3}[0-9]{1,3}' | sed 's/^(.*:)?(([0-9]{1,3}.){3}[0-9]{1,3}).*$/2/' | sort | uniq -c | sort -nr | sed 's/::ffff://' | head -20

If output shows any IP(s) having an excessive amount of connections to Apache that should not have that many connections, you might want to consider blocking the IP(s) within the server’s firewall. If you are experiencing a true DDoS (from multiple IPs), you should communicate with your datacentre, as they have specialized equipment to put in place to help mitigate the attack until it slows down or dies off.


